For many years, people assumed lInux was one of the most secure operating systems in the world. Even though the number of cyber attacks against Linux machines remains relatively small for now, several thousand machines were infected with malware, forcing them to send out spam messages. As we all know, spam messages – such as the ones sent through Mumblehard – are one of the more common causes of Bitcoin ransomware infections.
Also read: Coinify Partners With iSignthis to Enable Bitcoin Purchasing on Credit Cards
Mumblehard Linux Spam Botnet is No More
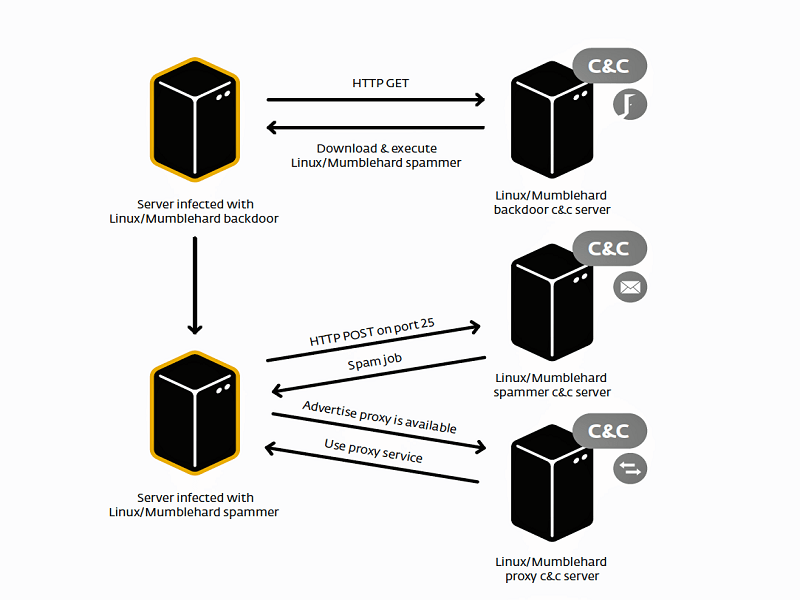
It has been over a year in the making, but Estonian law enforcement and the Eset security firm managed to put an end to the Mumblehard Linux botnet. Despite discovering this network of enslaved computer, it took quite some time to take control of the botnet, and eventually shut it down.
Mumblehard was a unique botnet sending spam email messages, as it used packed quite a punch once it managed to get installed on a Linux machine. Not only did the malware hide the source code from security solutions, but it also install backdoor access on infected computers, and a mail daemon used to get the spam messages sent to other computer users. In total, over 4,000 Linux computers were part of this botnet at its peak.
Similar to what security researchers have discovered in recent Bitcoin ransomware versions is how Mumblehard used command & control servers to coordinate the spam attacks. But that wasn’t the only purpose for these servers, as they sent messages to Spamhaus, asking for certain IP addresses to be delisted for having sent spam. Spamhaus employs a real-time composite blocking list, which adds IP addresses on a regular basis.
Eset researchers discovered the Mumblehard botnet made use of a script to monitor the Spamhaus CBL and see if botnet computers’ IP addresses were blacklisted. Although it is impossible to automate this process thanks to CAPTCHA protection, it appears the creators of this botnet found a way to circumvent this protection.
What is of particular concern is how the Eset security researchers are still not sure how the Mumblehard malware infected Linux computers all over the world in the first place. It was thought possible content management systems – such as WordPress – or any of its associated plugins had a security vulnerability that has been exploited. However, further investigation showed that was not possible, and the real answers remain elusive for now.
What are your thoughts on the Mumblehard Linux botnet? How were these machines infected? Let us know in the comments below!
Source: Ars Technica
Images courtesy of Ars Technica, Shutterstock