The recent hacking and defacing of the blog and Twitter account of Mt. Gox CEO Mark Karpeles, and the leaking of a 716 Mb archive file that allegedly contained trade data, database dumps, personal information about Karpeles, and an app for remotely accessing Mt. Gox data, has apparently been a clever ruse to make users download Bitcoin-stealing malware.
According to Kaspersky Lab expert Sergey Lozhkin, the file does contain (publicly available) data related to Mt. Gox trades, but also a Windows and a Mac Trojan.
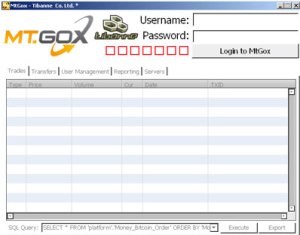
“When the victim executes the application, it looks like the back-office software for accessing the databases of Mt. Gox-s owning company, Tibanne Co. Ltd.,” he shared.
n the background, the malware creates and executes the TibanneSocket.exe binary and searches for bitcoin.conf and wallet.dat files on the target’s computer. If the latter file is found unencrypted, the criminals behind this scheme will easily access and steal the bitcoins stored in it.
The C&C server to which the information is exfiltrated is located in Bulgaria, but is currently offline.
This is not the first time that cyber crooks have taken advantage of Mt. Gox users’ desperation to scam the. Earlier this month scammers claimed that Mt. Gox will return all the lost Bitcoins, and urged users to watch a video detailing the process. In order to do so, they were required to download a fake and malicious Adobe Flash Player.
“Malware creators often using social engineering tricks and hot discussion topics to spread malware, and this is great example of an attack on a focused target audience,”
commented Lozhkin.
In fact, it seems that Mt. Gox users have already been targeted with phishing emails impersonating the exchange and asking them to share their name, address, username and password, and bank account number.
Author: Zejka Zorz
Source: net.security.org