
Over the years, crypto hacks have become more elaborate and common. In 2024, the community has seen hundreds of millions swept away from exploits and scams, leaving investors empty-handed.
Sometimes, the exploiters return the funds and point out a project’s vulnerabilities, helping prevent future incidents. However, it’s more common to see hackers take the stolen funds and flee the scene.
Crypto investigator ZachXBT unveiled a chain of exploits seemingly connected to the self-called Whitehat hacker responsible for the Prisma Finance exploit that took $12 million last month.
Stained Whitehat Hacker
On March 28, Prisma Finance, the Ethereum-based decentralized lending protocol, suffered a hack that stole 3,479.24 ETH. After being warned and observing the suspicious activity, Prisma’s team alerted the community.
At the time, the hacker contacted the Prisma team through an on-chain message, declaring to be a “Whitehat” looking out for users. During their conversation, the exploiter claimed they wanted to “raise better awareness on serious contract audits” and the use of DeFi.
The following day, the lending protocol released a detailed post-mortem of the incident. This post seemingly ruffled the hacker’s feathers, as they demanded that the team change all the “accusatory terms” like ‘exploit’ and ‘hacker.’
The messages raised alarms about whether the funds would be returned. Seemingly unsatisfied with the Prisma team’s compliance to edit the post-mortem post, the exploiter asked for a bounty of $3.8 million, worth 34% of the total funds.
1/ An investigation into the alleged $11.1M @PrismaFi exploiter 0x77 (Trung) and the multiple other exploits they are connected to. pic.twitter.com/QU1Oy7Txbb
— ZachXBT (@zachxbt) April 16, 2024
The amount asked was triple the industry standard of 10%. According to the crypto detective, the exploiter was “essentially extorting the team” as the treasury didn’t have enough funds to reimburse the victims.
Despite the Whitehat claims and apparent discomfort with terms that stated otherwise, the hacker contradicted himself by sending the funds to Tornado Cash. Further investigation by the crypto detective revealed that this Whitehat has several stains.
Prisma’s Exploiter Connected To Several Crypto Hacks
ZachXBT’s deep dive into the timing of related transactions resulted in the discovery of “activity connected to them on Tron.” One address, TGviNZ, was linked to numerous exploits.
Per the investigation, TGviNZ was funded by the Arcade_xyz exploit from March 2023. During this incident, the exploiter requested additional funds from the project via Telegram.
Similarly, the address was connected to the Pine Protocol exploit from February 2024. This time, the hacker asked for 50% of the funds and allegedly made “additional unreasonable requests over email.”
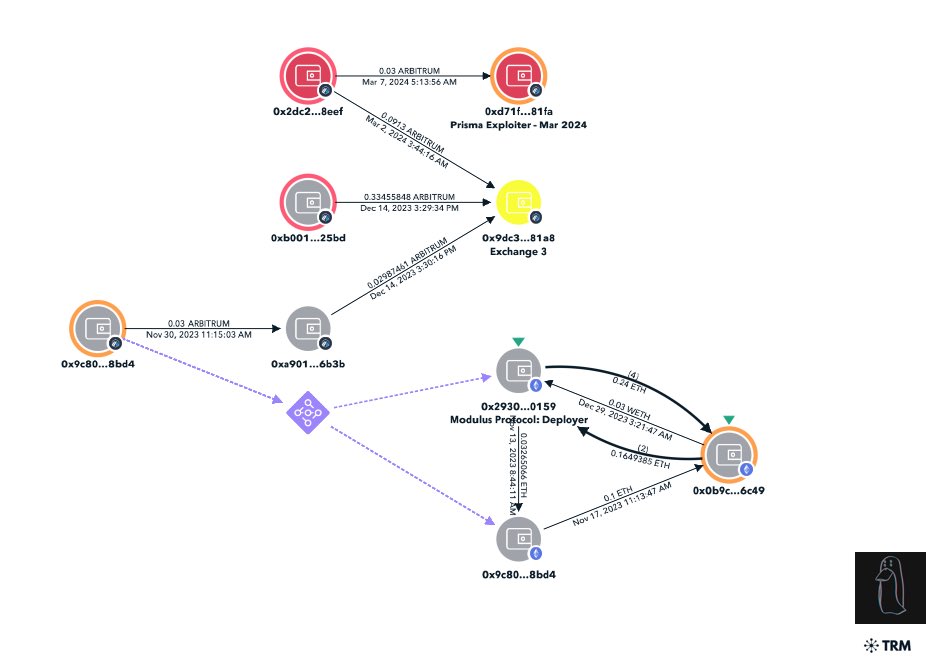
Chain of adresses connecting the Modulus Protocol deployer and the Prisma exploiter. Source: ZachXBT on X
The crypto sleuth then discovered that TGviNZ is linked to the deployer of Modulus protocol, a “decentralized, non-custodian platform.” Further investigation revealed that an X user, “0x77,” was among the few followers of the protocol.
This proved crucial in piecing together the puzzle, as the Arcade exploiter used the alias “0x77” on Telegram. A deeper look into the phone number, email addresses used, and other details pointed out the same suspect behind these exploits.
The details of the suspected exploiter are now in the hands of the Prisma team, which is investigating whether to pursue legal action against the individual in Vietnam and Australia.
Crypto Total Market Cap sitting at $2.207 trillion in the weekly chart. Source: TOTAL on TradingView


















