
Discussions about changing the dynamic code that runs the Bitcoin blockchain should constantly be happening. Over the course of the past year, the talks of changing the block size have been an overwhelming topic of conversation. There have been some pretty stubborn people when it comes to changing the protocols code, and this is not to say that forking the code is the right step. There has been censorship and subsequently has created a rift between people who want to raise the block size and those that don’t. In time, other discussions may have to occur regarding the underlying hash functions involved with the Bitcoin protocol and to assume things will always stay the same may be naive.
Also read: Stanford University Offers Bitcoin Course to Students
 One of the reasons they say behind not wanting to change the block size might be because it hasn’t been fully determined what Bitcoin will provide in the future. Will it be a currency that drives monumental exchange and super fast transactions or will it merely be a store of value? Allowing a code change could always pose a threat to its value and most importantly what it does. Tinkering with the code may be beneficial when it comes to figuring out Bitcoin’s best possible security solution with its partial quantum resistance. We have to take into consideration that this is not politics or some sort of psychological analysis. Cryptocurrency is about mathematics, and there is always an evolving force behind its science.
One of the reasons they say behind not wanting to change the block size might be because it hasn’t been fully determined what Bitcoin will provide in the future. Will it be a currency that drives monumental exchange and super fast transactions or will it merely be a store of value? Allowing a code change could always pose a threat to its value and most importantly what it does. Tinkering with the code may be beneficial when it comes to figuring out Bitcoin’s best possible security solution with its partial quantum resistance. We have to take into consideration that this is not politics or some sort of psychological analysis. Cryptocurrency is about mathematics, and there is always an evolving force behind its science.
Public key cryptography is used throughout the internet to secure websites, email, and multitudes of various transactions. Currently the two forms of cryptography that commonly secure our web is RSA and the Diffie-Hellman key exchange. These two methods are used in everything from cryptocurrencies financial transactions to the validation of software and legal documentation. This year the National Security Agency (NSA) has shown strong signs of moving in the direction of quantum resistant cryptography, and this is giving the internet a ghoulish scare.
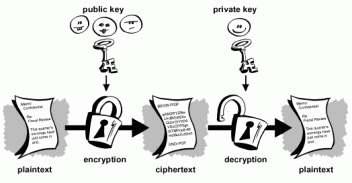 Quantum computing started taking shape in 1994 when Shor demonstrated efficient quantum algorithms that factored the computation of private logarithms. This demonstration had shown the world the universe of cryptography could be shaken by the use of quantum computers. A machine operating Shor’s algorithm in the future could easily factor numbers cracking common RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC). The NSA has been trying to build a quantum computer for a while now, and it’s no secret they are trying to crack all forms of the internet’s security. According to revelations told by former NSA employee Edward Snowden the intention to build a machine that cracks modern day cryptography is very real. So far the largest number factored by a quantum computer is 143 but Snowden says the threat still exists explaining the NSA’s research program costing 79 million which is entitled “Penetrating Hard Targets.” The NSA stated this past summer they strongly advise moving to the next set of cryptography research.
Quantum computing started taking shape in 1994 when Shor demonstrated efficient quantum algorithms that factored the computation of private logarithms. This demonstration had shown the world the universe of cryptography could be shaken by the use of quantum computers. A machine operating Shor’s algorithm in the future could easily factor numbers cracking common RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC). The NSA has been trying to build a quantum computer for a while now, and it’s no secret they are trying to crack all forms of the internet’s security. According to revelations told by former NSA employee Edward Snowden the intention to build a machine that cracks modern day cryptography is very real. So far the largest number factored by a quantum computer is 143 but Snowden says the threat still exists explaining the NSA’s research program costing 79 million which is entitled “Penetrating Hard Targets.” The NSA stated this past summer they strongly advise moving to the next set of cryptography research.
“Customers using layered commercial solutions to protect classified national security information with a long intelligence life should begin implementing a layer of quantum resistant protection.” ~ NSA, August 2015
Within the powerful new toolkits of decryption, the NSA’s quantum materials will supposedly be able to attack nearly all SSL, HTTP, and MySQL connections. Practical quantum computing is often told in theory however it’s not considered a fairytale this day in age and is becoming more of a real threat every day. In August of 2015, the NSA let the world know there was a need for post-quantum cryptography and certain methods should be abandoned in the coming years. Despite this statement, there has been no significant sign of anyone’s ability to crack the certain encryption they see as vulnerable. The elliptic curve P-384, RSA-3072, AES-256, SHA-384, and DH mod p 3072 all are under question as the NSA says they are safe for now but not for long.
 Bitcoin uses an Elliptic Curve Digital Signature Algorithm (ECDSA) for transaction verification. It also uses (RACE Integrity Primitives Evaluation Message Digest) RIPEMD with a digest size of 160 and Secure Hash Algorithm (SHA-256) for its hash function. Currently, ECDSA which is a Diffie-Hellman variant that produces our keys is seemingly the ‘possible backdoor’ for NSA agents to enter out of the rest of Bitcoin’s cryptographic functions. This attack is believed to be many years away if it can ever be broken outside of theory. SHA-256 a member of the SHA-2 family is a novel hash function in which the miners use to secure the network. The function is known to be collision resistant and is even further down the very distant future of ever being cracked. However, all of these cryptographic algorithms do have theoretical vulnerabilities, and their behavior is taken quite seriously in science and encryption communities. Weaknesses found in SHA-1 and MD5 were found by Wang Xiaoyun, who astonished the crowd at the CRYPTO 2004 event. Xiaoyun and co-authors had shown the world that these and several other hash functions were vulnerable to collision attacks and her research surprised everyone.
Bitcoin uses an Elliptic Curve Digital Signature Algorithm (ECDSA) for transaction verification. It also uses (RACE Integrity Primitives Evaluation Message Digest) RIPEMD with a digest size of 160 and Secure Hash Algorithm (SHA-256) for its hash function. Currently, ECDSA which is a Diffie-Hellman variant that produces our keys is seemingly the ‘possible backdoor’ for NSA agents to enter out of the rest of Bitcoin’s cryptographic functions. This attack is believed to be many years away if it can ever be broken outside of theory. SHA-256 a member of the SHA-2 family is a novel hash function in which the miners use to secure the network. The function is known to be collision resistant and is even further down the very distant future of ever being cracked. However, all of these cryptographic algorithms do have theoretical vulnerabilities, and their behavior is taken quite seriously in science and encryption communities. Weaknesses found in SHA-1 and MD5 were found by Wang Xiaoyun, who astonished the crowd at the CRYPTO 2004 event. Xiaoyun and co-authors had shown the world that these and several other hash functions were vulnerable to collision attacks and her research surprised everyone.
Bitcoin is partially quantum-safe and it’s ECDSA function could be changed over time and in theory so could it’s SHA-256. Theoretically ECDSA could be swapped with minor blows to the network with various temporary techniques like throw-away addresses. However, the implementation of changing out the SHA-256 algorithm could be catastrophic as it is the mining architecture of the entire ecosystem. It would take a lot of effort for a switch to say SHA-512 as the industry is dependent on the hardware specifically designed for the 256 algorithms. If there were a backdoor to SHA-256 our friend RIPEMD160 would allow developers time to try and do this swap but it’s timing would be critical.
 All of this doesn’t mean the end for Alice and Bob. But it means that thinking about changing code is not such a bad thing. Thinking and discussing is entirely different than actually doing. Those using censorship to rule their arguments are the real ones losing. If things are done without discussing the nature of the beast, then irrational decisions may be made and hastily when the time comes. The block size may have to be changed. ECDSA might have to be swapped someday and changed to something entirely different. One idea of dealing with this problem is the utilization of small pockets of concentrations in the alt-world. Altcoins can provide a test bed of blockchains implementing different ideas to strengthen the overall economy of Bitcoin.
All of this doesn’t mean the end for Alice and Bob. But it means that thinking about changing code is not such a bad thing. Thinking and discussing is entirely different than actually doing. Those using censorship to rule their arguments are the real ones losing. If things are done without discussing the nature of the beast, then irrational decisions may be made and hastily when the time comes. The block size may have to be changed. ECDSA might have to be swapped someday and changed to something entirely different. One idea of dealing with this problem is the utilization of small pockets of concentrations in the alt-world. Altcoins can provide a test bed of blockchains implementing different ideas to strengthen the overall economy of Bitcoin.
Discussing how the block size increase may or may not speed up the amount of transaction processing time is a discussion that must be had. Vulnerabilities in ECC could definitely be a threat in the future and figuring out the best possible scenario should probably be a wise researched decision before it’s too late. Dynamic software is made to change all the time and conforming to no change at all can be dangerous to the evolution for certain technologies. The block size discussion is happening today. Tomorrow we may be discussing the security of the underlying cryptography itself. Or should we now?
What do you think about changing the code? Let us know in the comments below.
Images courtesy of Shutterstock, Pixbay, and Redmemes


















